Moving from Legacy to UEFI Boot
My home media PC is running on old hardware which wasn’t really an issue. But, recently, it started messing with me. So, I decided to move it to a (slightly) newer computer. And this should be as easy as transferring disk. But, in my case I used legacy boot on the old system and the new system only does UEFI. So, in order for disk transplant to take, I had to first move to UEFI on the old computer.
Fortunatelly, Microsoft actually has a half decent answer. But, more importanty, it also provides you with a tool to automate the process. Call me a chicken, but I am always worried when I touch my partitions.
First, you need to boot into the recovery environment. In theory, this should be possible by holding a <Shift> key. In practice, I rarely succeed using this method. What I found works more reliably is simply turning off machine in the middle of the boot. It’s a bit of a brute force solution but, after two unsuccessful boots, Windows will hapilly cooperate.
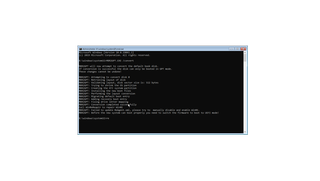
Once you boot into the Windows Recovery environment, you need to go Troubleshoot, Advanced, Command Prompt. There you can run validation command:
mbr2gpt.exe /validateThis command will let you know if anything is unsupported with your setup. If you have a standard Windows installation, you’ll be fine. If you have extra partitions on your boot drive, you might want to remove them before proceeding.
Once your validation passes, we can trigger the conversion from MBR to GPT which, in this case, also means changing the boot from legacy to UEFI.
mbr2gpt.exe /convertThis command will be done in less then a minute. You might get a warning about WinRE but don’t worry about that right now. Next, you power off the system using Turn off your PC option.
When you start system the next time, you will probably need to go into BIOS (F2 or Del usually do the trick). Now you can select UEFI boot option and disable the old Legacy one. Short reboot later, your Windows should boot using UEFI.
Now you can sort out the WinRE warnng by disabling and re-enabling it again.
reagentc /disable
reagentc /enable