Fixing MPV Playback from Samba Share
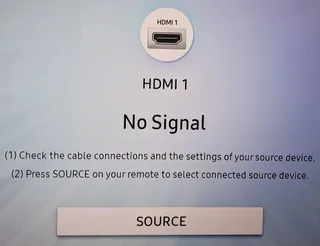
Running KDE is usually quite troublefree. However, on my new install I faced unusual problem. My photos and media on samba share simply would not open. I could see text files just fine. But no movie for me.
Interestingly, this behavior seemed limited to MPV and Haruna. Other media players seemed unaffected by whatever afflicted them. It took a bit of investigation but I traced the issue to the following line in their .desktop file:
X-KDE-Protocols=ftp,http,https,mms,rtmp,rtsp,sftp,smb,srt,rist,webdav,webdavsWhile they both claim to understand samba protocol (smb), removing it from supported protocols actually solved the issue. It seems that my samba server was simply not to their liking. After doing a bit of investigation, I am still puzzled why exactly - especially since it works just fine on another computer. Some dependency is missing and, while finding it would be possible, it would also waste my time when I already have solution.
Just removing smb works like a charm:
sudo sed -i 's/,smb,/,/g' /usr/share/applications/mpv.desktop
sudo sed -i 's/,smb,/,/g' /usr/share/applications/org.kde.haruna.desktopIt’s a temporary fix but Kubuntu 26.04 is just around the corner anyhow.