Nexus 4 owners are a bit itchy these days. KitKat is out but nobody got it as an update yet. However, we are step closer to that since Google posted official factory images. If you are prepared to lose all your data, you might as well update OS yourself. I will describe this procedure on Windows and on non-developer’s computer.
NOTE: THIS PROCEDURE WILL DELETE ALL THE CONTENT ON YOUR PHONE.
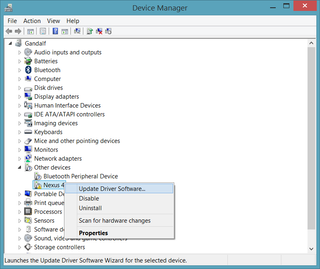
We’ll definitely need to download Google’s USB drivers. Once you download and unpack the archive, you’ll need to go to Device Manager and find your Nexus device with an exclamation point next to its name. Right-click, Update Driver Software, and select location where you unpacked the driver zip file. Your device should then be named Android ADB Interface.
And we definitelly need ADB and Fastboot tools. While we can get them in Google SDK, I found that Minimal ADB and Fastboot works nicely and it is less fuss to install on a non-developer computer. Just execute installation and do standard Next, Next, Finish dance routine.
Last, but not the least, we need factory image itself. Once downloaded, I usually just unpack it in same directory as Minimal ADB and Fastboot (C:\Program Files (x86)\Minimal ADB and Fastboot on my computer) to avoid setting up the paths (yep, pure laziness).
Next order of business is enabling USB debugging. This means going to Settings, About phone and clicking Build Number 7 times. Your Nexus 4 will pronounce you a developer and you will get additional Developer options in Settings. There you must turn on USB debugging. As soon as that is done, device will ask you for confirmation.
Once allowed, we can go start Minimal ADB and Fastboot command line (or just reuse one automatically started after setup). There we will first check whether device is visible:
adb devices
* daemon not running. starting it now on port 5037 *
* daemon started successfully *
List of devices attached
04caa50d9f0c7784 device
Assuming device is visible, we’ll reboot into bootloader:
adb reboot-bootloader
Device will go down and you will be presented with a nice screen that probably says LOCK STATE - locked in the last line. We can change that with a simple unlock command:
fastboot oem unlock
...
OKAY [ 30.008s]
finished. total time: 30.009s
Moment of truth is upon us. Now we run update itself:
flash-all.bat
sending 'bootloader' (2203 KB)...
OKAY [ 0.072s]
writing 'bootloader'...
OKAY [ 0.333s]
finished. total time: 0.409s
rebooting into bootloader...
OKAY [ 0.003s]
finished. total time: 0.005s
< waiting for device >
sending 'radio' (45537 KB)...
OKAY [ 1.437s]
writing 'radio'...
OKAY [ 2.578s]
finished. total time: 4.018s
rebooting into bootloader...
OKAY [ 0.002s]
finished. total time: 0.003s
< waiting for device >
archive does not contain 'boot.sig'
archive does not contain 'recovery.sig'
archive does not contain 'system.sig'
--------------------------------------------
Bootloader Version...: MAKOZ30d
Baseband Version.....: M9615A-CEFWMAZM-2.0.1700.97
Serial Number........: 04caa50d9f0c7784
--------------------------------------------
checking product...
OKAY [ 0.002s]
checking version-bootloader...
OKAY [ 0.003s]
checking version-baseband...
OKAY [ 0.002s]
sending 'boot' (6336 KB)...
OKAY [ 0.202s]
writing 'boot'...
OKAY [ 0.365s]
sending 'recovery' (6884 KB)...
OKAY [ 0.238s]
writing 'recovery'...
OKAY [ 0.411s]
erasing 'system'...
OKAY [ 0.568s]
sending 'system' (700500 KB)...
OKAY [ 22.124s]
writing 'system'...
OKAY [ 42.031s]
erasing 'userdata'...
OKAY [ 0.810s]
formatting 'userdata' partition...
Creating filesystem with parameters:
Size: 14129561600
Block size: 4096
Blocks per group: 32768
Inodes per group: 8144
Inode size: 256
Journal blocks: 32768
Label:
Blocks: 3449600
Block groups: 106
Reserved block group size: 847
Created filesystem with 11/863264 inodes and 95427/3449600 blocks
sending 'userdata' (137438 KB)...
writing 'userdata'...
OKAY [ 12.716s]
erasing 'cache'...
OKAY [ 0.043s]
formatting 'cache' partition...
Creating filesystem with parameters:
Size: 587202560
Block size: 4096
Blocks per group: 32768
Inodes per group: 7168
Inode size: 256
Journal blocks: 2240
Label:
Blocks: 143360
Block groups: 5
Reserved block group size: 39
Created filesystem with 11/35840 inodes and 4616/143360 blocks
sending 'cache' (10984 KB)...
writing 'cache'...
OKAY [ 1.042s]
rebooting...
finished. total time: 80.594s
Press any key to exit...
Congratulations! Your device is a KitKat.
After this I prefer to make myself a developer and enable USB debugging once more. In a new Minimal ADB and Fastboot command line (because flash-all batch closed our last one), reboot to bootloader and lock it again:
adb reboot-bootloader
fastboot oem lock
...
OKAY [ 0.010s]
finished. total time: 0.011s
Simple power button press later and our device is exactly where we started; minus lost data and plus an android version.