Changing FAT12 Label Under NAS4Free
Part of my encrypted NAS setup is also key storage on TmpUsb. Idea of such USB is to self-erase its data (and thus my encryption keys) when power is lost. It’s not a full-proof system but enough to ensure any thief will get away with hardware only.
TmpUsb device behaves just as a normal USB drive with a twist that label changes are triggering various special behaviors. If one is setting up such disk remotely, the most significant operation is done by changing label to “ARMED” to actually make it erasable upon power loss.
And therein lies the problem - NAS4Free contains no command that can change the label for FAT12 disk. Well, I guess we’ll have to make such command ourselves.
First a bit about FAT12 disk layout. Looking at the raw drive, the first 512-byte sector is occupied by master boot record. There we have layout of our partitions and their types. The only byte I am interested in is the partition type for the first partition located at the 451th position and holding a value 0x01 and denoting FAT12. This byte is important as to avoid accidentally overwriting some other disk upon label change.
The next two sectors belong to the FAT12 boot sector and are filled by a lot of important information. However, the label we’re searching for cannot be found albeit there is a very similar volume label field. Here we can also see, starting at byte 54, a type of file system. This time it’s written as FAT12 and is ideal as another double-check.
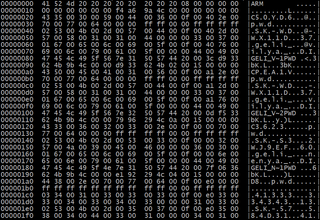
Nope, the paydirt is in fourth sector, the first 11 bytes are ones holding the disk label we need. You can see the whole sector using dd and hexdump:
dd if=/dev/da0 bs=512 skip=3 count=1 2>/dev/null | hexdump -CvThe rest of sector (and a few afterward) are filled with directory entries using both short 8.3 MS-DOS name and long Unicode one. Quite interesting topic actually, but we need only to care about the first 11 bytes here.
The final script I ended up with actually uses dd internally and allows for setting custom label under NAS4Free’s limited FreeBSD environment. As it’s using bog standard bash, I expect it’s perfectly portable to other platforms too and modifying to do other manipulations of FAT structures should be easy enough.
And, as always, it’s available for download.
[2018-07-22: NAS4Free has been renamed to XigmaNAS as of July 2018]