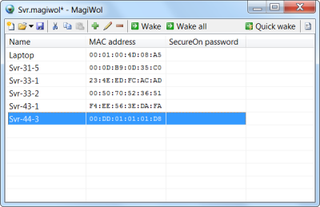
Hohm Beta
While ago I applied for beta of Hohm. Site looked like nice utility. You would (I assume) put list of your home appliances and site would calculate how much electricity you are using.
However, it seems that people from Croatia are not worthy of those calculations since to sign up you need valid postal code. Although it is not written clearly anywhere it became clear to me that Croatian postal code is no-no.
Maybe there is valid reason why only U.S.A. is supported by this web site. Maybe it is political decision - I am fine with this also. What I am not fine with is Microsoft sending me “sign up today” message while it has Croatia in my profile. Is it so hard to filter your non-U.S.A. customers and not send them an invitation?