Should You Take Password Advice From a Comic?
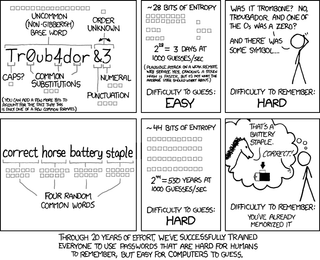
Many have seen comic on the right explaining how to select a good password. Some might have even seen security expert Bruce Schneier claiming it is a wrong approach. And then there were several rebuttals. It was as close to celebrity fight as it comes in the computer industry.
As somebody who implemented password generator and a junkie for a good statistics, I’ll dare to throw bit of my opinion here.
For analysis, first thing we need to know is how fast you can crack passwords. And here assumption of 1000 guesses per second mentioned in cartoon is highly optimistic. Mind you, it is not wrong, as it specifies online attack and assumes proper hash used for computation. But, more often than not, your password will leak in one of stolen database dumps. Now attacker can do stuff offline.
With the advent of graphic cards and massively parallel processing, I believe we can go with assumption of 100 x 1012 guesses per second for basic MD5 hashing. Yes, it is highly exaggerated if password uses any stronger hash, but in the case of password strength analysis it is best to be paranoid and assume not only lousy hashing but a strong attacker with access to many computers. And do check this video to see what a “simple” server can do - it peaks at 38 billion (38 x 109) guesses per second. For a single server.
Now we take claim from cartoon of its password having entropy of 244 (17 x 1012) we can see that attacker can go over that whole search space within 5 hours assuming usage of the server from video. Using our imaginary powerful attacker, same space can be searched in less then a second. Does that mean XKCD was really wrong? Well, it’s kinda complicated…
Assumption we made is that attacker knows exact dictionary and exact way how you selected your password. Baring that, you have 25 character password that, using brute force only, would require checking of (on average) 1 x 1035 combinations. That means even our all-powerful attacker would need 30,000,000,000,000 years (again, on average) to find it. More observant might have noticed that there is a slight disparity between 1 second and 30 trillion years.
Issue at hand is how well the attacker knows you and what “rules” it feeds to its cracking engine. If it has all these words in its dictionary and it assumes you used comic as a password selection authority, you’re toast. However, if guy goes for low-hanging fruit, it will ignore everything longer than 12-14 characters and your password is safe.
And anything you add is going to make that long phrase only better. Add a three digit number at the end, you increase time by the factor of 1,000. Add it anywhere in the middle, you increase it by factor of 25,000. Add a special character, complexity goes up still. And that is for somebody who perfectly knows how your password was created. While XKCD method alone is a bit too optimistic, it is on the right track. If you select password you can remember and you spice it enough, brute force cannot touch you.
But I believe what comic omits is one important fact. Developers are lazy and some just simply don’t care. It is not uncommon for password leaks to have no password hashing at all. If you use the same password for multiple sites, sorry but you are fucked no matter which password you have.
First important rule about passwords is to never ever reuse them. Every site must have a unique password. This ensures that any password leak, even if developers were extremely lazy, only impacts a single account. For example, prevents attacker using your leaked LinkedIn password to login to your PayPal.
Second rule is to never, ever, know more than one password. XKCD is correct, humans are simply not made to handle passwords. So don’t. Remember one password and use a password manager to create and manage others.
You can use my own Bimil or you can use Password Safe - they both actually use the same file format. Or you can use something else you feel is secure enough. But, for the love of god, don’t use your web browser for remembering any password you don’t wish to leak.
PS: If you wish to be informed when your password leaks, do consider subscribing to ';–have i been pwned?. It won’t protect you, but it will at least keep you informed.